International Travel
U.S. Customs and Border Protection may search and copy the contents of travelers' laptops and expect travelers to divulge credentials and encryption keys as necessary. Americans can expect similar treatment when visiting other countries. Refusal to comply can result in seizure of the device or denial of entry into the host country. Once in the country, risks to confidential, controlled and sensitive data continue. Some countries legally prohibit encryption, and others view all encryption suspiciously. Physical loss and digital espionage also put confidential information (or tools to access it) on your devices at risk.
When traveling abroad, there is no expectation of privacy. Always assume in your destination country, U.S. ports of entry and in transit, eavesdropping may take place on all electronic communications.
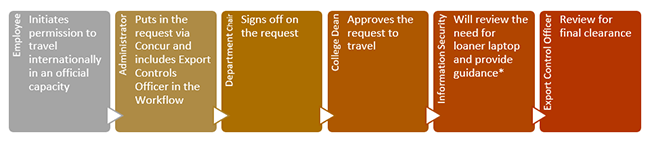
International Travel Request Process
Faculty or staff member travelling internationally you need to follow the approval process
Prepare for International Travel
- Start your International Travel Request
- Use a Loaner Device- International travelers should arrange to use loaner devices while traveling abroad. Load only essential data and information that will be needed while traveling and be sure to set password controls.
- Do not travel with confidential or sensitive information even if it is encrypted - U.S. export control regulations forbid the transport of certain data outside of the country (see the ITS Helpdesk Portal website to request a device).
- Do not allow services or applications to store your passwords on the loaner device.
- No Loaner Device Available?- If loaner devices are not available, take the following steps to prepare your system for international travel:
- Back up all data.
- Remove all information not essential to travel. Do not travel with confidential, sensitive, proprietary, research or export controlled information even if it is encrypted. U.S. export control regulations forbid the transport of certain data outside of the country (see the Texas A&M University-San Antonio- Division of Research website for information).
- Do not allow services or applications to store your passwords. Remove this option for your current systems, including email and Wi-Fi.
- Update all antivirus, security patches, and firewalls.
- Set up password protection on your devices. Require a password to start and unlock the device.
- Receive Office of Information Security approval memorandum
- Enroll in MFA (Multifactor Authentication) for work and personal accounts
How to protect your resources during International Travel
- Keep Devices with You- Do not leave any electronic devices (cell phones, laptops, tablets, etc.) unattended, even in your hotel room or safe. Do not pack electronic devices in your checked bags or ask someone to watch them for you.
- Be Wary of Public Wi-Fi- Wi-Fi hotspots for public use are targets for information theft. While on public Wi-Fi, your device is vulnerable to data miners. You should connect to a Virtual Private Network (VPN) whenever possible or avoid visiting websites that contain confidential information, such as banking websites, to keep your information secure.
- Disconnect When Possible- Turn off Bluetooth, cellular services and Wi-Fi any time you are not using them.
- Limit Access to Restricted Information- To prevent the interception of information without your knowledge, avoid accessing confidential, sensitive, proprietary, research or export-restricted information from your electronic device. If you must access these items for presentations or collaboration, use a secure A&M-SA VPN connection, unless encryption is prohibited in the host country (see the Texas A&M University-San Antonio- Division of Research website for more information).
- Loss or Theft - Immediately report loss or theft of electronic devices to the local authorities and your departmental IT staff. Do not wait until your return to report loss or theft. Take the necessary contact information with you and store it separately from your electronic devices.
What to do after International Travel
- Return any loaner devices - Remove all data from your loaner devices and return them promptly.
- Change Your Passwords- Change your password on any service, device or application that you accessed while traveling or that shares a password that you used while traveling.
- Sanitize Your Devices- When possible, reinstall the Operating System on any devices you carried on your trip. Otherwise, request that an IT person analyze your device for malware or unauthorized access.